What is Crowdsec?
CrowdSec is an open-source and lightweight software that allows you to detect peers with malevolent behaviors and block them from accessing your systems at various levels (infrastructural, system, applicative).
To achieve this, CrowdSec reads logs from different sources (files, streams …) to parse, normalize and enrich them before matching them to threats patterns called scenarios.
One of the advantages of CrowdSec when compared to other solutions is its crowd-sourced aspect: Meta information about detected attacks (Source IP address, time, and triggered scenario) is sent to a central API and then shared amongst all users.
Thanks to this, besides detecting and stopping attacks in real-time based on your logs, it allows you to preemptively block known bad actors from accessing your information system.
Installing Crowdsec on a server
Centos Flavor Install Detect Mode only:
#Install Crowdsec
#Full Docs https://docs.crowdsec.net/docs/getting_started/install_crowdsec/
curl -s https://packagecloud.io/install/repositories/crowdsec/crowdsec/script.rpm.sh | sudo bash
yum install crowdsec -y
#Change Default Port from 8080 to 8888
#so it doesn't conflict with Plesk or other setups we have.
sed -i 's/8080/8888/' /etc/crowdsec/config.yaml
sed -i 's/8080/8888/' /etc/crowdsec/local_api_credentials.yaml
cscli collections install crowdsecurity/whitelist-good-actors
cscli parsers install crowdsecurity/whitelists
#False alarms on magento sites and others: http-crawl-non_statics
sed -i 's/capacity: 40/capacity: 100/' /etc/crowdsec/scenarios/http-crawl-non_statics.yaml
#speed up sql lite performance
sed -i '/^db_config:/a \ use_wal: true' /etc/crowdsec/config.yaml
systemctl restart crowdsec
#Show Decisions
cscli decisions list
#show autodiscovered services.
cscli metricsDepending on server use case also add these:
cscli collections install crowdsecurity/magento
cscli collections install crowdsecurity/dovecot
cscli collections install crowdsecurity/wordpress
sudo systemctl reload crowdsecPlesk – Additional Steps
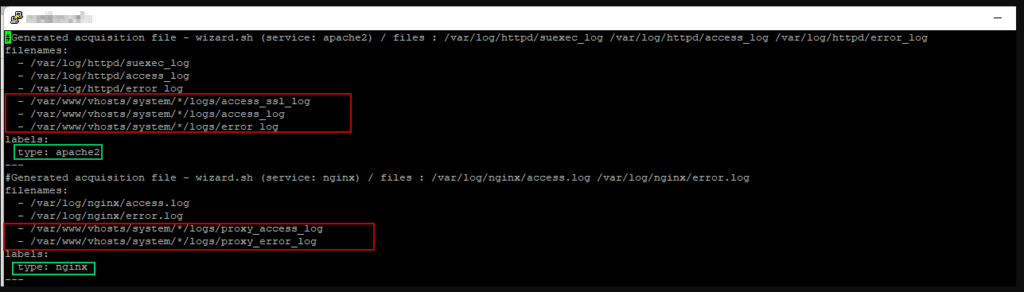
vi /etc/crowdsec/acquis.yamlFind the section labelled apach2 and add the below:
- /var/www/vhosts/system/*/logs/access_ssl_log
- /var/www/vhosts/system/*/logs/access_log
- /var/www/vhosts/system/*/logs/error_logFind the section labelled nginx and add:
- /var/www/vhosts/system/*/logs/proxy_access_log
- /var/www/vhosts/system/*/logs/proxy_error_logReload the config:
sudo systemctl reload crowdsecExample Of how the config should look:
We are only in DETECT mode so far.
You can monitor what is found for a day or two.
cscli decisions list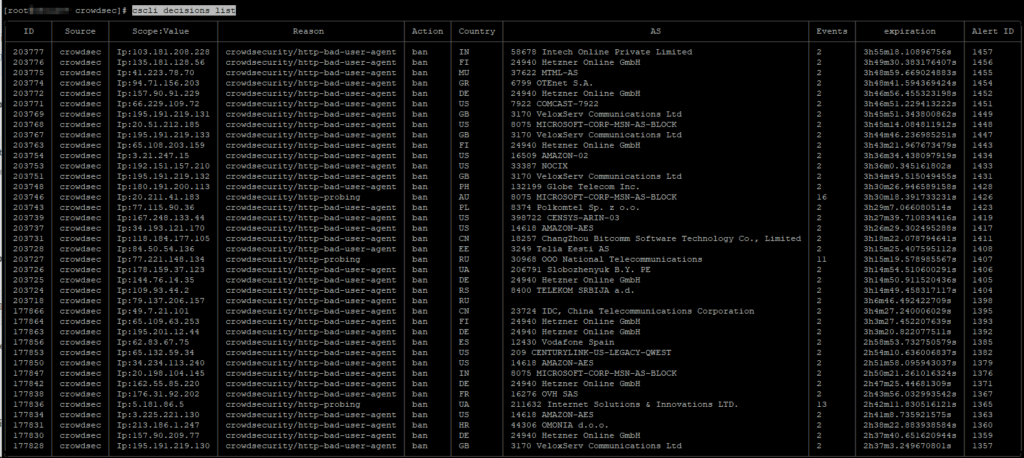
Activate Block Mode
Here we assume your using iptables and not cloudflare in front of the site. Crowdsec does support cloudflare and has a guide for it.
#add the bounder
yum install -y crowdsec-firewall-bouncer-iptables
systemctl enable crowdsec-firewall-bouncer
#if apf
#then we need to add
[ -d "/etc/apf/" ] && echo "/bin/systemctl restart crowdsec-firewall-bouncer" >> /etc/apf/postroute.rules
#if csf:
[ -d "/etc/csf/" ] && echo '#!/bin/bash' >> /etc/csf/csfpost.sh && echo "systemctl restart crowdsec-firewall-bouncer" >> /etc/csf/csfpost.shUnblock an IP
cscli decisions delete --ip X.X.X.XNeed to turn off Crowdsec Enforcement all together for an urgent scanario?
systemctl stop crowdsec-firewall-bouncerIf running apf or csf, Then make sure to comment out the line restarting it in csf or apf by vi’ing the correct file below:
apf: /etc/apf/postroute.rules
csf: /etc/csf/csfpost.sh
Troubleshooting
If a specific scenario is giving alot of false alarms (perhaps due to the way the site is built), you may want to turn that one off.
#List all scenarios
cscli scenarios list
#turn off the specific one
cscli scenarios remove crowdsecurity/http-path-traversal-probingCommon false alarms and fixes
http-crawl-non_statics – the default value can be too low so change it from 40 to 100.
sed -i 's/capacity: 40/capacity: 100/' /etc/crowdsec/scenarios/http-crawl-non_statics.yaml
sudo systemctl reload crowdsechttp-generic-bf – with certain wordpress page builders we have seen admin users ip get blocked due to 403 calls. Let’s make our own rule set and then restart crowdsec.
vi /etc/crowdsec/parsers/s02-enrich/cd-whitelist-403-wp-admin-ajax.yaml
name: creatingdigital/wp-admin-ajax-403-whitelist
description: "Whitelist events from admin ajax"
filter: "evt.Meta.service == 'http' && evt.Meta.log_type in ['access_ssl_log']"
whitelist:
reason: "CD wp-admin-ajax-403 Whitelist"
expression:
- evt.Meta.http_status == '403' && evt.Meta.http_verb == 'POST' && evt.Meta.http_path == '/wp-admin/admin-ajax.php'service crowdsec restartWhitelist an IP
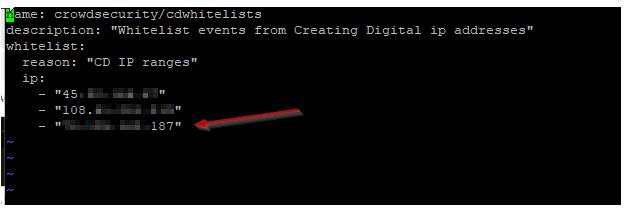
Create our own rule file:
vi /etc/crowdsec/parsers/s02-enrich/cdwhitelists.yaml